CMMC Level 1 – Nuts and Bolts

Before we begin, it important to note that different frameworks have different nomenclature and IDs for the controls they contain. The FAR items and CMMC Level 1 requirements tie back to NIST 800-171 controls and those are the identifiers we’ll be referencing in the rest of the article.
Core Area & Controls
As described in the CMMC Level 1 Overview blog post there are 10 key strategies to achieving compliance.
Key Strategies for Compliance
- Know Your Assets: Understand what needs protection.
- Train Your Users: Educate employees on the importance of handling FCI.
- Enable Multi-Factor Authentication: Add an extra layer of security.
- Restrict Admin Privileges: Limit access to sensitive information.
- Regularly Update Systems: Stay on top of software and OS patches.
- System Hardening: Secure your IT infrastructure.
- Network Segmentation: Isolate critical systems and data.
- Reliable Backups: Regularly back up data and test recovery plans.
- Monitor Systems: Stay vigilant for any signs of a breach.
- Vendor Management: Ensure your third parties are also compliant.
Describe & Catalog your Systems
Consider all assets that process, store, or transmit FCI ‘in-scope’ for any CMMC assessment. The best way to ensure you identity all the places and ways you need to protect data is to think about how each data type is:
- received/generated
- stored
- accessed/handled
- distributed
- disposed
Don’t skim over this step. Start with a thorough assessment of how data is used and moves in and out of your organization, so you can accurately answer the rest of the assessment questions and determine what is in scope.

Once the scope is confirmed, you can describe the technical systems in place for all IT systems/assets.
This is going to involve developing a clear and detailed IT system inventory, including third party tools that may assist with backup, encryption, etc.
You must:
- Develop a full list (via spreadsheet or automated compliance tools)
- Define processes and procedures for maintaining the list (if not automated)
- Enforce maintenance of the list
Confidentiality
Access Control
Access is about protecting the confidentiality of FCI. The vast major of control needed for CMMC Level 1 are in this area. See Control List below and remember:
- Document policy, procedure, and process to describe HOW you will meet the control.
- Set up automation/tracking to gather proof that you consistently meet the controls as outlined.
- To be secure, you must follow all outlined processes OVER TIME and set up checks and balances to ensure it
People & Devices
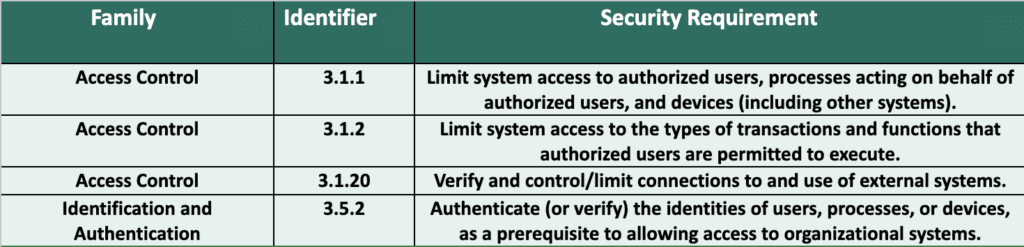
Types of data you will track:
- Updated list of users and devices (MDM tooling is helpful here).
- Maintain an updated list of accounts/credentials centrally, including any shared credentials (which should be avoided), detailing their usage, and identifying who has access to them.
- Confirmation of use of 2FA on all systems or notation of any exceptions.
- Regular review of access to ensure consistent application of least privilege.
- Track changes to firewall rules and the addition of new assets to ensure their placement in the correct network segment.
Physical
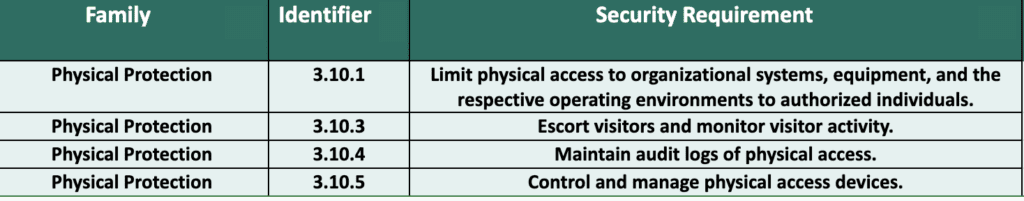
You may or may not need to document the controls in this section if you do not have a physical office location. Many SaaS based companies are fully remote and therefore can mark these controls as out-of-scope.
This is an area that is often lacking the depth needed to satisfy CMMC Level 1. Implement common-sense measures like locking doors and windows, but also ensure monitoring and logging of all facility entries under CMMC Level 1. This includes not only known visitors but also potential malicious intrusions detected through security cameras, motion sensors, badge access controls, and key inventories. Train employees to properly grant and document visitor access. Make it clear that the controls in place will hold individuals accountable for allowing undocumented guests into the facility or for any actions that are suspicious, malicious, or violate stated policies.
Network / Systems
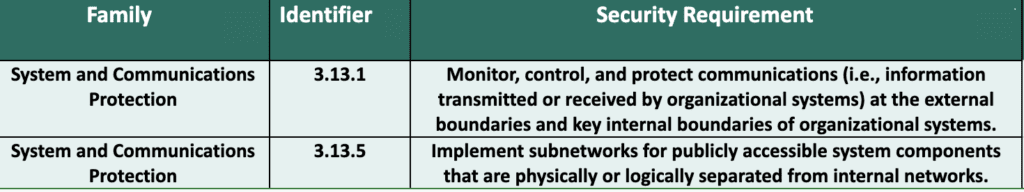
The final access-related controls concern the protection of digital assets, specifically central company assets processing or storing FCI. Configure servers, cloud storage, and applications to block access in the event a malicious actor breaches an end-user device, a single tool, or a network segment. You may satisfy this control by verifying with vendors that necessary controls are in place. However, if you manage any cloud storage/processing directly, you must secure your perimeter. This may include:
- Network Segmentation
- Check firewalls for allowed and blocked inbound and outbound connections.
- Penetration Testing (to confirm configuration and segmentation)
Accidental release of FCI
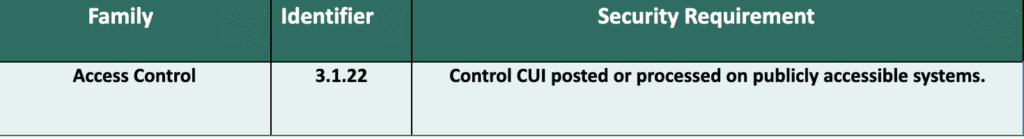
Tools are available to help you control what data leaves your organization but unfortunately humans remain the key to controlling data release. Employee information security training is CRITICAL to keeping your organization secure. This should include structured training and phishing campaigns to regularly test your employees and create a culture of security.
Integrity
Prevent tampering
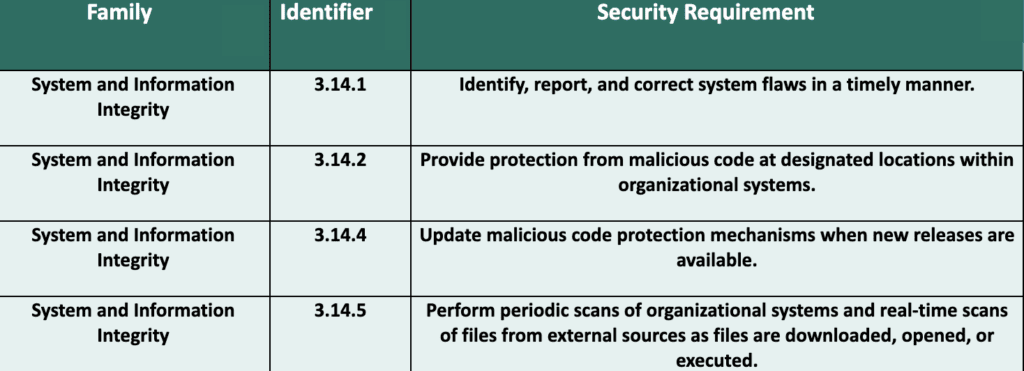
Reduce the likelihood of devices and systems being compromised
- Block the introduction of malicious code with antivirus products and mail attachment protection.
- Regularly update antivirus tools with the latest signatures.
- Conduct application scanning more frequently than full Penetration Testing.
- Address known vulnerabilities through a robust patching program, removal of end-of-life products, regular scanning for new vulnerabilities, and establishing clear rules for fixing vulnerabilities.
MDM tools can help with these controls on personal devices like laptops – one product can check off access control, hardening and malicious code avoidance controls. Penetration testing and automated tools can ensure shared/central systems remain compliant and are properly hardened. Standard controls typically detected by scanning tools include: avoiding default administrative usernames and passwords, employing strong encryption for internal communication, disabling unused ports, and limiting access to open ports. Document defaults for new devices as a standard practice.
Again it comes down to maintenance and documented proof. How do you generate to-do items upon discovering flaws? How do you ensure their completion within the timeframe your policies and procedures mandate? How do you monitor timely patching after vendor releases? What are your hardening standards, and how do you verify their implementation on new devices?
Availability

This control directly addresses the Federal standards for destroying media no longer needed, highlighting the crucial security principle of data availability. To ensure proper handling, you must define your data, understand its retention period, and confirm its expiration before destruction.
Destruction may just mean deleting the data from cloud servers. If you release hardware from your control (laptops, phones you own, server hard-drives) then you must ensure FCI data is unrecoverable from the hardware. You can learn more about the process, known as ‘sanitizing’ the hardware, by reading NIST 800-88.
CMMC Level 1 in Summary
Start by downloading our basic checklist, but remember, being secure involves more than just ticking off the 17 items listed for CMMC Level 1. Read our overview blog post to learn more about what Viridis Security believes are the “sleep at night” basics you should be considering and reach out to learn how we can help.

hbspt.forms.create({
region: “na1”,
portalId: “43533991”,
formId: “d830f9f4-b26f-45b0-9617-f583f8dd8062”
});
