How long does it take to achieve SOC 2 compliance?

How long does it take to achieve SOC 2 compliance? Achieving SOC 2 compliance is a significant milestone that underscores your organization’s commitment to cybersecurity excellence and data protection. The SOC 2 audit process can be intricate and demanding, but with the right preparation and guidance, it’s an achievable goal. Here’s a comprehensive guide to […]
SOC 2 + The Digital Operational Resilience Act

SOC 2 + The Digital Operational Resilience Act For a fintech customer that is already SOC 2 Type II compliant, transitioning to DORA (Digital Operational Resilience Act) compliance will require implementing additional controls and adapting existing processes to meet the specific regulatory requirements of DORA. While SOC 2 focuses on security, availability, processing integrity, confidentiality, […]
Navigating the Transition to NIST 2.0: A Guide for Modern Governance

NIST Cybersecurity Framework (CSF) 2.0 marks a significant evolution in cybersecurity practices.
SOC 2 Managed Programs
Why SOC 2 Compliance Partnering Works
SOC 2 Implementation
Five Stage Implementation Process
Crafting Organization Risk Appetite Statements

An effective risk appetite statement does more than outline the thresholds of risk acceptance. It serves as a strategic document that aligns with an organization’s mission, vision, and strategic direction.
Are your Automated Compliance tools enough?
Automated Compliance tools are only as good as the people that wield them. Without Information Security, Governance, Risk and Compliance experience, you risk being overconfident in your control environment.
Unpacking the Limits of Automated Compliance Tools
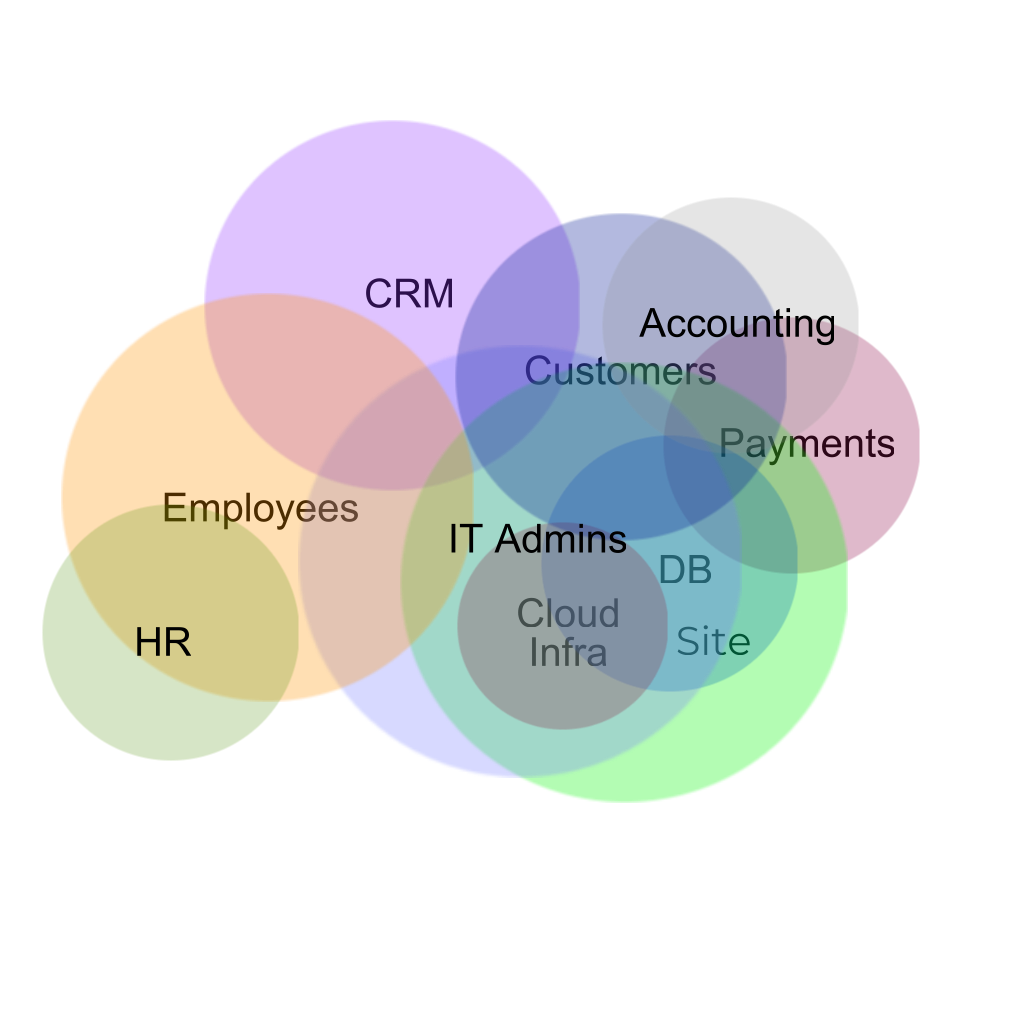
There are limits to automated compliance tools and viridis security vciso services can fill the gap
Vendor (3rd Party) Assurance Tracker – Part 2
Part 2 tutorial for the google form based vendor assurance tracker for third party vendor management
CMMC Level 1 – in depth

CMMC Level 1 details and download of compliance checklist. FCI, CUI, FAR, NIST 800-171